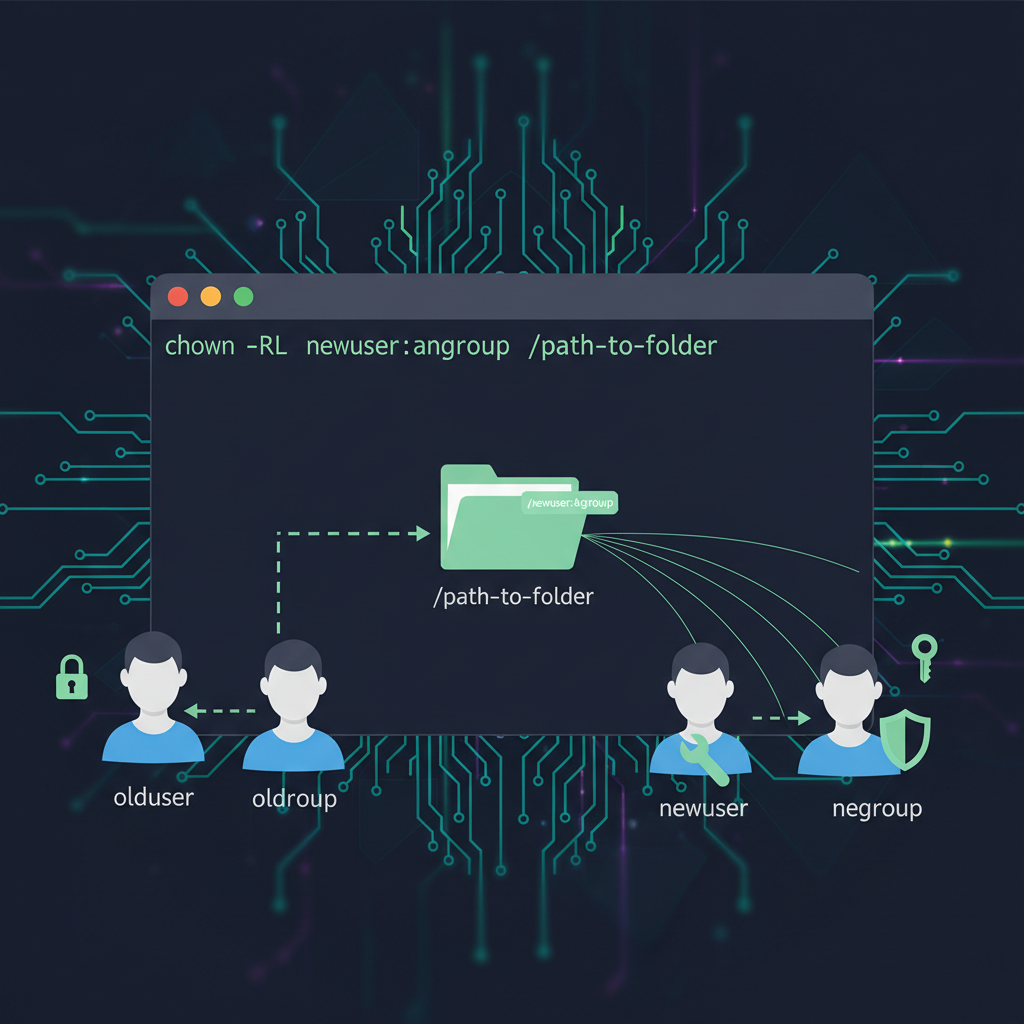
Demystifying systemd-resolved: A Comprehensive Guide to Local DNS ResolutionHey there, fellow Linux enthusiasts! Alice here, ready to dive deep into another fascinating corner of the Linux world. Today, we're tackling systemd-resolved, a system service that provides local DNS resolution. If you've ever wrestled with DNS configuration, especially in complex network environments, this guide is…
Read more